|
|
5 tahun lalu | |
|---|---|---|
| img | 5 tahun lalu | |
| src | 5 tahun lalu | |
| .gitignore | 5 tahun lalu | |
| Cargo.lock | 5 tahun lalu | |
| Cargo.toml | 5 tahun lalu | |
| README.md | 5 tahun lalu |
README.md
Shellc0der
Installation
$ git clone https://git.swrzm.de/msc/shellc0der
$ cd shellc0der
$ cargo run
Usage
shellc0der -i <input.bin> -o <output.bin>
- The input/output files are raw (non-encoded) shellcode
Function
This encoder supports several ways of changing the original shellcode:
- Block Reordering
- Payload Encoding
- Instruction Substitution
- Dead Code Insertion
The default functionality is the following:
- 1) Divide the shellcode into blocks and reorder them
- 2) Encode the full payload
- 3) Generate unique decoder stub, insert dead code, switch instructions, ...
- 4) Combine the stub and the encoded payload and write it to the output file
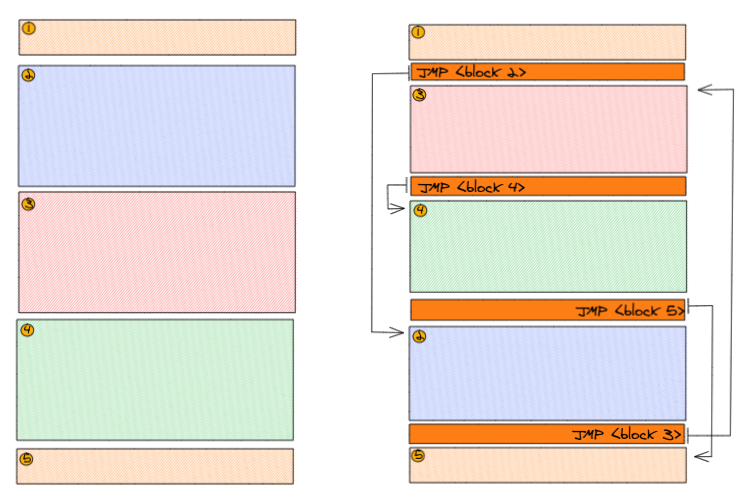
Block Reordering
Block reordering works in the following way:
- 1) Disassemble the payload (using capstone)
- 2) Check for all JMP, Loop, JCC instructions and patch the destination by inserting newl generated labels
- 3) Devide the instructions in blocks of X instructions each.
- 4) The first and the last block stay the same
- 5) The middle-blocks are randomly shuffled and glued together with
JMPinstructions
It looks somewhat like that:
Payload Encoding
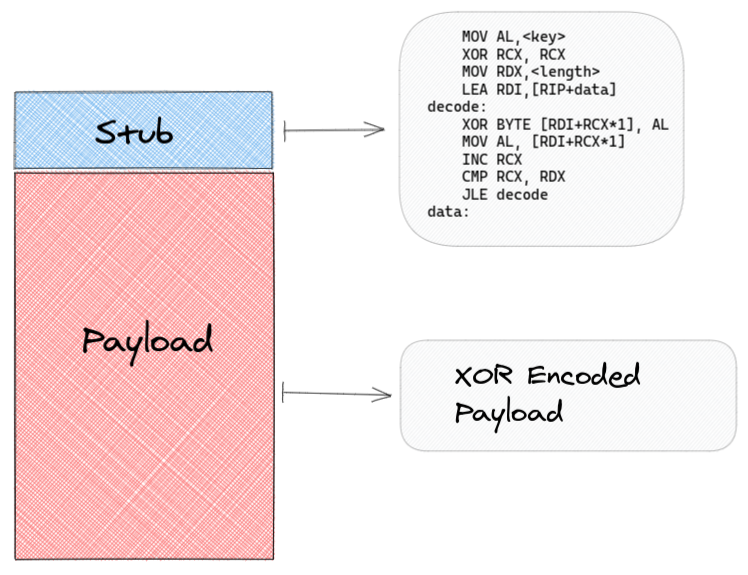
The basic structure of the encoded shellcode looks like this:
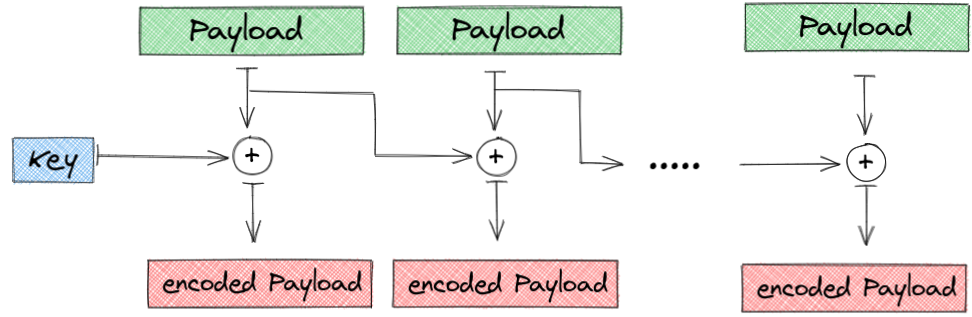
- 1) The initial shellcode gets encoded via XOR, in the following way:
Note: Every Block is a single byte
- 2) A random decoder-stub is generated, that is setup in front of the encoded payload
- 3) The registers used in the stub are randomly generated on each run
- 4) Additionally, dead code snippets (random snippets & random # of snippets) are inserted into the stub
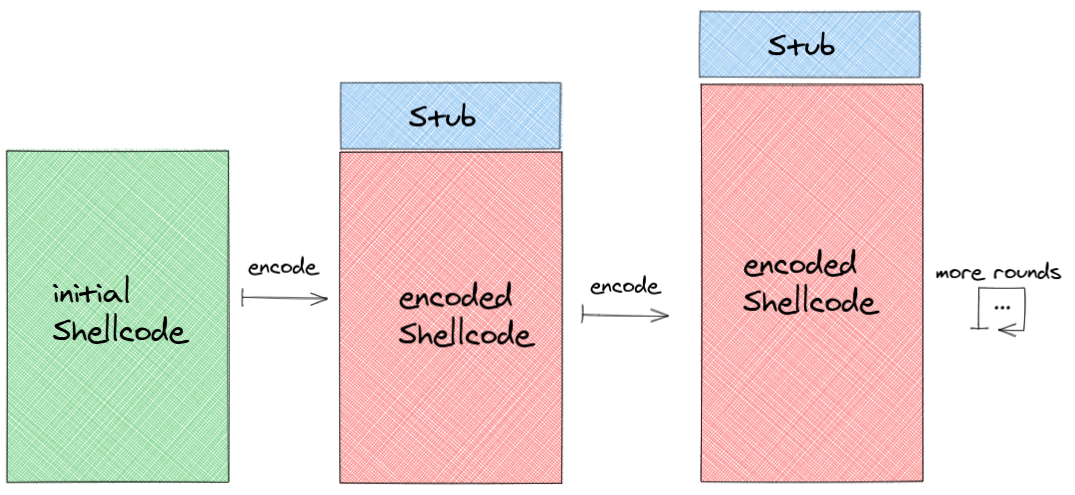
- 5) Steps 1-4 can be repeated for arbitrary rounds, as seen below:
Credits
The inspiration came from:
- ShikataGaNai by Metasploit-Framework
- https://github.com/EgeBalci/sgn