|
|
%!s(int64=5) %!d(string=hai) anos | |
|---|---|---|
| img | %!s(int64=5) %!d(string=hai) anos | |
| src | %!s(int64=5) %!d(string=hai) anos | |
| .gitignore | %!s(int64=5) %!d(string=hai) anos | |
| Cargo.lock | %!s(int64=5) %!d(string=hai) anos | |
| Cargo.toml | %!s(int64=5) %!d(string=hai) anos | |
| README.md | %!s(int64=5) %!d(string=hai) anos |
README.md
DNS Tunnel
DNS
This contains a short implementation of the DNS protocol, inspired by the documentation from @EmilHernvall https://github.com/EmilHernvall/dnsguide/blob/master/chapter5.md
Tunnel
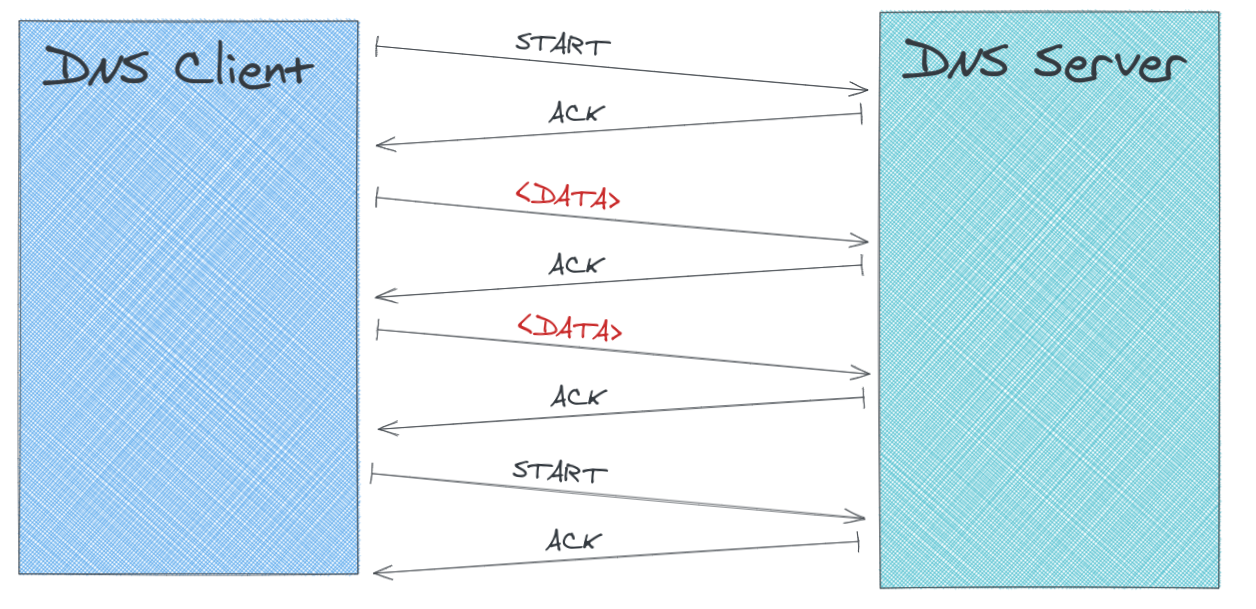
The basic tunnel is looking like that:
The tunnel is communicating only via TXT records, sending data happens in the following steps:
Client -> Server
1) Client sends a DNS Question for the TXT record to INIT.domain.com to check if the server answers
2) For a correct answer, the TXT Record must be set to ACK
3) Sending a payload consists of the following messages:
- DNS Request with `START.domain.com`
- DNS Reply with `ACK`
- DNS Request with `somedatahere.domain.com`
- DNS Request with `somedatahere.domain.com`
- ...
- DNS Request with `END.domain.com`
- DNS Reply with `ACK`
Server -> Client
1) The client sends regular POLL requests
2) The server will provide the data to send in the TXT Record
3) Approach is the same:
- DNS Request with `POLL.domain.com`
- DNS Reply with `START`
- DNS Request with `POLL.domain.com`
- DNS Reply with `herecomesthedata`
- DNS Request with `POLL.domain.com`
- DNS Reply with `herecomesmoredata`
- DNS Request with `POLL.domain.com`
- DNS Reply with `END`
For the complete communication, the data is first "encrypted" via xor() and then base64 encoded to hide
the payload at least a little bit