|
|
@@ -0,0 +1,39 @@
|
|
|
+---
|
|
|
+title: Cracking WPA2
|
|
|
+categories: [cheatsheets]
|
|
|
+tags: [security, wireless]
|
|
|
+---
|
|
|
+
|
|
|
+# Cracking WPA2
|
|
|
+
|
|
|
+## 4-way Handshake
|
|
|
+
|
|
|
+Explained in greater detail @ [https://wlan1nde.wordpress.com/2014/10/27/4-way-handshake/](https://wlan1nde.wordpress.com/2014/10/27/4-way-handshake/)
|
|
|
+
|
|
|
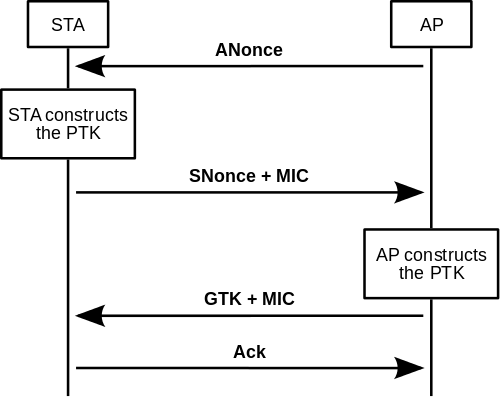
+The 4-way handshake looks like this:
|
|
|
+
|
|
|
+
|
|
|
+
|
|
|
+The handshake is used to exchange key-data between AP and Client.
|
|
|
+Transient keys are derived from a master key, the Pairwise Master Key (PMK).
|
|
|
+In case of WPA-PSK this is the WiFi password.
|
|
|
+
|
|
|
+## Capturing handshakes
|
|
|
+
|
|
|
+
|
|
|
+
|
|
|
+
|
|
|
+## Converting Handshakes
|
|
|
+
|
|
|
+* Usefull tool for playing with handshakes, pcap-files, ...: hcxtool
|
|
|
+
|
|
|
+* Convert pcap to hccapx file (used for hashcat)
|
|
|
+
|
|
|
+```
|
|
|
+hcxpcaptool -o output.hccapx handshake.pcap
|
|
|
+```
|
|
|
+* Convert pcap to john the ripper hash (`--format=wpapsk`)
|
|
|
+
|
|
|
+```
|
|
|
+hcxpcaptool -o output.hccapx handshake.pcap
|
|
|
+```
|